What’s the Difference Between BEC and Regular Phishing?
The other day I was asked to partake in a “working group” about business email compromises also known as “BEC”. The first topic that came up was the difference between BEC and phishing emails. After further discussion on the differences, my confusion prompted me to write a blog on these two topics.
BEC is a form of phishing, however, unlike regular phishing campaigns, BEC victims are typically a C-Suite, executive, or someone holding a position tied to finances. The purpose of a BEC campaign is to be hyper-focused on the target while causing the largest impact on the infrastructure.
Unlike regular phishing campaigns where an attacker is sending out large amounts of spam to a large group of people, BEC operations are extremely intentional and focused on the target victim(s). That is why on a per attack basis, BEC is far more costly than regular phishing.
So what cyber actors are partaking in such attacks?
One of the cybergangs using BEC is from West Africa and referred to as Silent Starling. They are known for swindling more than 500 organizations by utilizing a technique known as vendor email compromise (VEC). Here is a white paper with more information, Link. We will cover VEC another time, for now, back to BEC.
Current BEC Activities: Some of the types of trends seen recently are scams associated with the procurement of personal protective equipment (PPE) and gift cards. Gift cards are the most popular target of BEC crime and COVID has been a great help to increase sales for eCriminals.
This technique works by first having the email appear to be coming from a “boss” or someone in a position of power. Next, the email will provide details as to what the victim needs to do and provide “evidence” it is coming from the said sender. Figure 1.
Figure 1: Example of a BEC
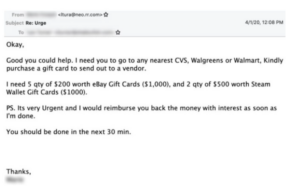
Recommendations: This email does have some similarities with a regular phishing email, however, does it smell a normal ‘phish’ or something more? So, what can you do to check? Ask before you buy anything. Message the sender directly and confirm they sent the email. Next, have an SOP or defined guidance in your organization to reference, explicitly stating whether you can purchase these items using your personal and/or corporate card without prior approval in written form. When in doubt confirm, confirm, confirm.
Additional Resources: Here is a great white paper from Phishlabs about BEC attacks: Link